Introduction: Why SaaS Data Security Matters
SaaS adoption has exploded—by 2025, the average enterprise uses over 130 SaaS applications across departments. But with rapid adoption comes greater risk: insider threats, misconfigured APIs, poor tenant isolation, and data breaches that can cost millions.
Security is a survival strategy for SaaS companies; it is not a choice. Consumers anticipate that platforms would securely handle sensitive data while adhering to laws such as GDPR, Build HIPAA-Compliant, and SOC 2. Regulatory sanctions and harm to one's reputation can result from a weak architecture.
This article provides a complete breakdown of SaaS security architecture patterns that protect data while enabling scalability and compliance.
TL;DR – Quick Answer
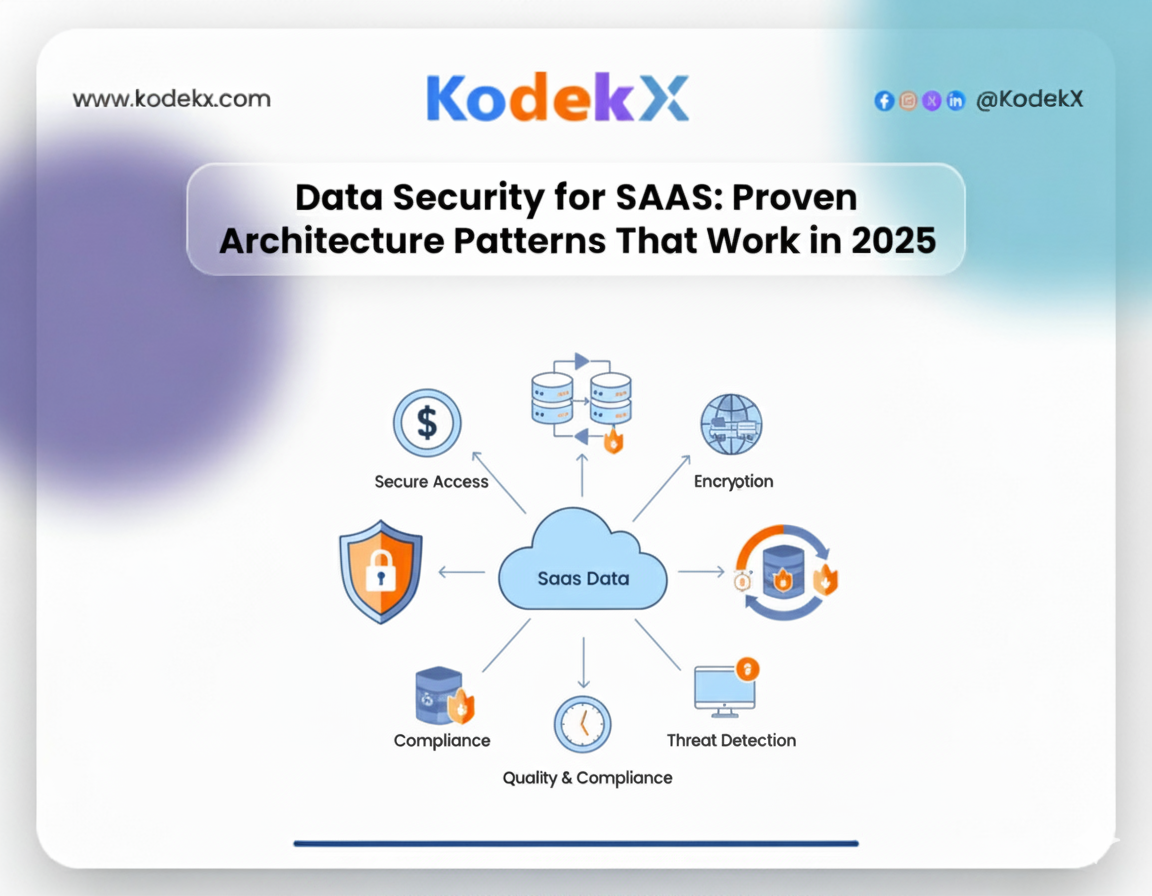
To secure SaaS data effectively, companies must combine MFA, Zero Trust, CASBs, SSPM tools, RBAC, multi-tenancy models, and encryption. Continuous monitoring, auditing, and incident response ensure ongoing protection. These architecture patterns form a layered defense model, aligning with industry leaders like Palo Alto, Fortinet, and Splunk.
SaaS Security: What & Why
Cloud-hosted apps and their user data are protected by a set of rules, technologies, frameworks, and architectural patterns known as SaaS (Software-as-a-Service) security. Because SaaS platforms are always-on, Build multi-tenant SaaS architecture, and internet-facing, they are more susceptible to changing cyberthreats than traditional on-premises software.
Why SaaS Security Matters
From startups using Slack and Notion for collaboration to large corporations handling sensitive data in Salesforce, Workday, or Microsoft 365, SaaS adoption has exploded across industries. Every SaaS provider must guarantee the confidentiality, integrity, and availability (CIA) of data while adhering to stringent regulatory and customer trust standards, which comes with this expansion.
Key Challenges in SaaS Security
- Data Isolation Across Tenants
In multi-tenant SaaS systems, a single database often serves multiple customers (tenants). Poor isolation can lead to cross-tenant data leaks—a nightmare scenario for both providers and customers.
- Access Control for Thousands of Users
Large SaaS applications often serve tens of thousands of concurrent users. Enforcing role-based access control (RBAC), multi-factor authentication (MFA), and adaptive authorization is essential to prevent privilege abuse.
- Regulatory Compliance (GDPR, HIPAA, PCI DSS)
Global SaaS products must navigate complex regulatory landscapes. For example, GDPR demands strict data residency and deletion rights, HIPAA enforces healthcare data privacy, and PCI DSS governs payment data handling.
- Cloud Provider vs. SaaS Provider Responsibility
Security in SaaS follows a shared responsibility model. Cloud service providers (like AWS, Azure, GCP) secure the infrastructure, while SaaS vendors must secure applications, identity, and data. Misunderstanding this balance often leads to exploitable gaps.
The Goal of SaaS Security Architecture
The ultimate objective is to design a security framework that balances protection, Software Scalability, and performance. Too much friction (like excessive verification steps) can frustrate users, while weak controls expose data to breaches. A strong SaaS security model:
- Protects data in transit and at rest through encryption.
- Implements Zero Trust and least privilege principles.
- Automates compliance checks with SaaS Security Posture Management (SSPM) tools.
- Continuously adapts to evolving threat vectors without slowing down business operations.
In essence, SaaS security isn’t just about locking down systems—it’s about enabling trust at scale.
Key Security Facts & Highlights
- 99% of account compromises involve missing MFA (Microsoft, 2023).
- Zero Trust adoption reduces breach likelihood by 50% (Forrester, 2024).
- CASB adoption grew 40% between 2022–2023 (Gartner).
- SSPM automation cuts compliance workload by 60%.
- RBAC and access control prevent 80% of insider incidents (Ponemon Institute).
Core Architecture Patterns for SaaS Security
Multi-Factor Authentication (MFA)
- Reduces unauthorized access risks by requiring multiple verification methods.
- Should support adaptive MFA for high-risk logins.
- Phishing-resistant MFA (e.g., hardware keys) recommended.
Zero Trust Model
- Principle: Never trust, always verify.
- Continuous identity verification and micro-segmentation.
- Prevents lateral movement inside SaaS systems.
Cloud Access Security Brokers (CASBs)
- Provide visibility & control over SaaS data movement.
- Functions: Access control, data encryption, threat detection, DLP.
- Essential for securing SaaS-to-SaaS integrations.
SaaS Security Posture Management (SSPM)
- Automates compliance checks across multiple SaaS apps.
- Provides centralized dashboards for monitoring.
- Prevents shadow IT risks by identifying unapproved SaaS usage.
Role-Based Access Control (RBAC)
- Limits access to sensitive data based on roles.
- Enforces least-privilege principles.
- Requires periodic permission reviews.
Multi-Tenancy Security Models
- Shared DB, Shared Schema → MVPs/startups (lower cost, less isolation).
- Shared DB, Separate Schemas → growing SaaS apps (balanced security).
- Separate DBs → enterprises with compliance needs (highest security).
Best Practice: Always scope ORM queries by tenant_id.
Data Encryption (At-Rest & In-Transit)
- TLS for in-transit protection.
- AES-256 or customer-managed keys (BYOK) for at-rest encryption.
- Field-level encryption for PII (e.g., social security numbers).
Monitoring, Auditing & Incident Response
- Real-time monitoring tools detect anomalies.
- Audit logs track access and modifications.
- Incident response plans must include playbooks for SaaS breaches.
Training & Awareness Programs
- 90% of breaches involve human error.
- Conduct phishing awareness campaigns.
- Require strong passwords + password managers.
Real-World Examples & Case Studies
- Slack: Implements tenant isolation + RBAC to secure enterprise data.
- Salesforce: Encrypts at-rest data with customer-controlled keys.
- Microsoft 365: Uses CASBs + SSPM for SaaS visibility and compliance.
- Zoom: Migrated from shared-schema to per-DB model for enterprise clients.
Comparison of SaaS Security Architecture Options
| Security Pattern | Best For | Pros | Cons |
|---|---|---|---|
| Shared DB, Shared Schema | Startups / MVPs | Low cost, fast to deploy | Weak isolation, compliance risk |
| Shared DB, Separate Schemas | Mid-size SaaS apps | Stronger isolation, moderate cost | Complex migrations |
| Separate DBs | Enterprises, regulated apps | Maximum isolation, compliance-ready | Higher cost, ops overhead |
Common Pitfalls and How to Fix Them
- Pitfall: Relying only on passwords.
Fix: Enforce MFA + SSO.
- Pitfall: Over-privileged accounts.
Fix: Apply RBAC + quarterly access reviews.
- Pitfall: Misconfigured storage buckets.
Fix: Automate checks with SSPM tools.
- Pitfall: Tenant query leaks.
Fix: Scope ORM queries with tenant IDs.
- Pitfall: Reactive security.
Fix: Adopt Zero Trust + Proactive Monitoring Telemetry Pipelines.
Competitive Insights: What Leaders Are Doing
- Palo Alto Networks – Focuses on security audits, MFA, encryption, IAM.
- Fortinet – Defines six levels of SaaS security: cloud, network, server, app, data, user.
- Netguru & Aalpha – Emphasize multi-tenancy and scalability as core to SaaS security.
- Splunk – Advocates Zero Trust + MFA as core strategies.
- Ramotion & Acropolium – Show how architecture choices (monolithic, microservices, serverless) impact security.
- Microminder – Stresses security reviews for multi-tenancy risks.
- Apriorit – Highlights database design for SaaS data security.
These competitors reinforce that security architecture is the competitive differentiator in SaaS success.
Methodology – How We Compiled This Guide
To ensure this guide delivers both depth and practical relevance, we followed a structured research process that combined competitive analysis, industry standards, and real-world SaaS practices. We began by carefully studying more than ten leading blogs and whitepapers on SaaS security, including detailed resources from Palo Alto Networks, Fortinet, Splunk, Netguru, and Microminder. These sources provided insights into the current state of SaaS security, common threats, and the best practices already being discussed in the industry.
After that, we compared those results to internationally accepted security frameworks including the OWASP Top 10 for SaaS apps, the Cloud Security Alliance (CSA) principles, and the NIST Cybersecurity Framework. This alignment made sure that the suggestions made here are both realistic and in line with the most widely accepted cybersecurity standards in the world.
We used data and projections from reputable research firms like Gartner and Forrester, as well as security insights from industry giants like Microsoft, to bolster our findings. These resources ensured that this guide is based on quantifiable, evidence-based data rather than conjecture by helping to validate the trends we saw and offering quantitative support for our assertions.
Lastly, we compared these results to actual SaaS security methods utilized major international platforms like Salesforce, Zoom, and Slack. We were able to link theoretical best practices with tried-and-true operational tactics by examining how these businesses handle multi-tenancy concerns, apply Zero Trust, and handle compliance at scale.
The result is a guide that is not just academic in nature but firmly grounded in both research and practical application—giving SaaS founders, developers, and security leaders a clear, actionable framework to strengthen their security posture.
The Path Forward in SaaS Data Security
SaaS data security is now a multi-layered, dynamic defense approach rather than a single control or item on a checklist. A variety of steps must be taken to safeguard cloud-based apps and client data in order to stop unwanted access, identify questionable activities, and react to problems promptly. Multi-factor authentication (MFA) and role-based access control (RBAC) are fundamental security procedures that guarantee only the appropriate individuals have access to the appropriate resources. The chance of account compromise, which is still one of the most popular access gates for attackers, is significantly decreased by these restrictions.
Organizations must then move into more complex models like Cloud Access Security Brokers (CASBs), which offer insight into data flows and enforce policies across many SaaS apps, and Zero Trust, where each access request is continuously validated. These steps establish a robust yet adaptable security posture that can change when new threats appear.
As SaaS platforms scale, so too must their defenses. This is where SaaS Security Posture Management (SSPM) tools and tenant-level isolation become critical. SSPM automates compliance checks, monitors security configurations in real time, and reduces the human error that often leads to breaches. Meanwhile, tenant isolation ensures that in multi-tenant environments, data belonging to one customer remains fully separated from another, eliminating the risk of cross-tenant leakage.
Without ongoing monitoring, frequent audits, staff training, and a solid incident response plan, even the most robust technical protections are obviously insufficient. These components complete the circle, guaranteeing that security is both proactive and reactive, capable of promptly containing and mitigating any compromise.
The path forward for SaaS providers is clear: start with the essentials, grow into advanced architectures, and never stop evolving. Secure your SaaS today by evaluating your current architecture, enforcing Zero Trust principles, and building trust with customers through strong, transparent security practices. By doing so, you not only protect sensitive data but also strengthen customer confidence—the most valuable currency in the SaaS ecosystem.
Summary
SaaS adoption is booming, but with growth comes heightened security risk. Modern enterprises use over 130 SaaS applications, creating challenges like tenant isolation, access control, regulatory compliance, and the shared responsibility model between cloud providers and SaaS vendors. Weak architectures not only expose businesses to data breaches and regulatory fines but also erode customer trust.
Effective SaaS security requires a layered defense strategy. Core measures include multi-factor authentication (MFA), role-based access control (RBAC), Zero Trust, Cloud Access Security Brokers (CASBs), and SaaS Security Posture Management (SSPM). These must be combined with encryption, tenant-level isolation, monitoring, auditing, employee training, and strong incident response plans. This layered approach ensures data confidentiality, integrity, and availability without sacrificing scalability or user experience.
Industry leaders like Palo Alto Networks, Fortinet, Splunk, and Microsoft emphasize Zero Trust adoption, CASB integration, and compliance automation. Real-world platforms such as Slack, Salesforce, Microsoft 365, and Zoom demonstrate best practices in tenant isolation, encryption, and posture management.
In the end, SaaS security is about establishing trust at scalable MVP development, not just about protection. Providers can protect client data, adhere to international compliance standards, and establish a competitive position in the market by implementing robust, proactive security infrastructures. Moving from simple controls like MFA to sophisticated structures backed by ongoing automation and monitoring is the way forward.
References
Protect SaaS Data Smartly
Build trust with proven 2025 security patterns.
Frequently Asked Questions
Many organizations assume the cloud provider alone handles all security. In reality, SaaS security is a partnership: the cloud vendor is responsible for securing infrastructure, physical hardware, and the base platform. The SaaS provider (or customer) must secure application layers, user access, data, and configuration. Misunderstanding where responsibility ends often causes security gaps.
Multi-tenancy allows multiple customers (“tenants”) to share the same software instance, infrastructure, or database. Ensuring isolation means using architecture patterns like separate schemas or separate databases, implementing strict tenant_id scoping in all queries, isolating storage (e.g. per-tenant buckets), and using role-based and attribute-based access control so one tenant cannot access another’s data.
Zero Trust is a security model where no user or device is inherently trusted, even if inside the network. Every access request must be authenticated, authorized, and verified. For SaaS, this means continuously validating user credentials, using MFA, monitoring session behavior, and segmenting access between services. It’s vital because it reduces risk from compromised credentials, insider threats, or lateral movement in the system.
Encryption must be applied both in transit (TLS) and at rest (strong algorithms like AES-256). Sensitive fields (PII, financial, health data) may require field- or column-level encryption. Key management should use trusted systems (e.g., cloud KMSs, HSMs) and support practices like key rotation. In some cases, customers want BYOK (Bring Your Own Key) to retain more control.
A secure SaaS environment needs real-time or near-real-time monitoring of user activity, configuration changes, and anomalous behavior. Audit logs should be immutable and include tenant and resource metadata. Regular audits (internal and external) help identify trends or misconfigurations. Incident response plans must be documented, tested, and have defined playbooks so that when a breach or misstep occurs, the team can respond quickly, contain damage, and restore operations.